Access Graph resources across tenants without secrets or certificates!
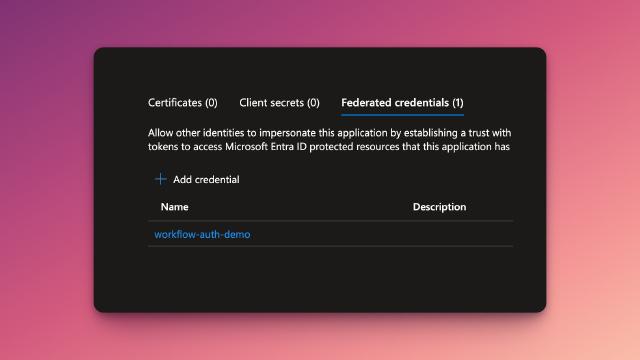
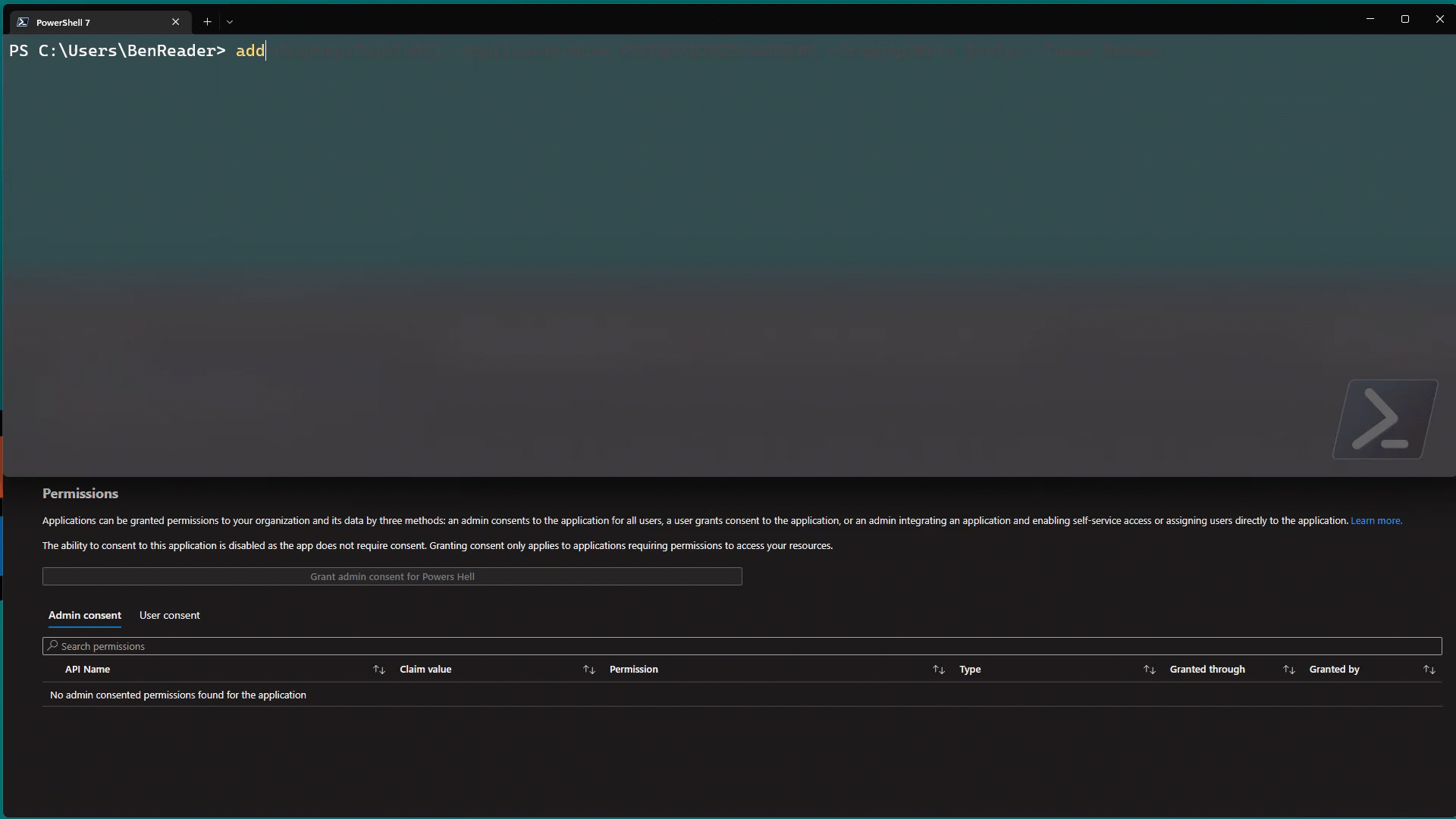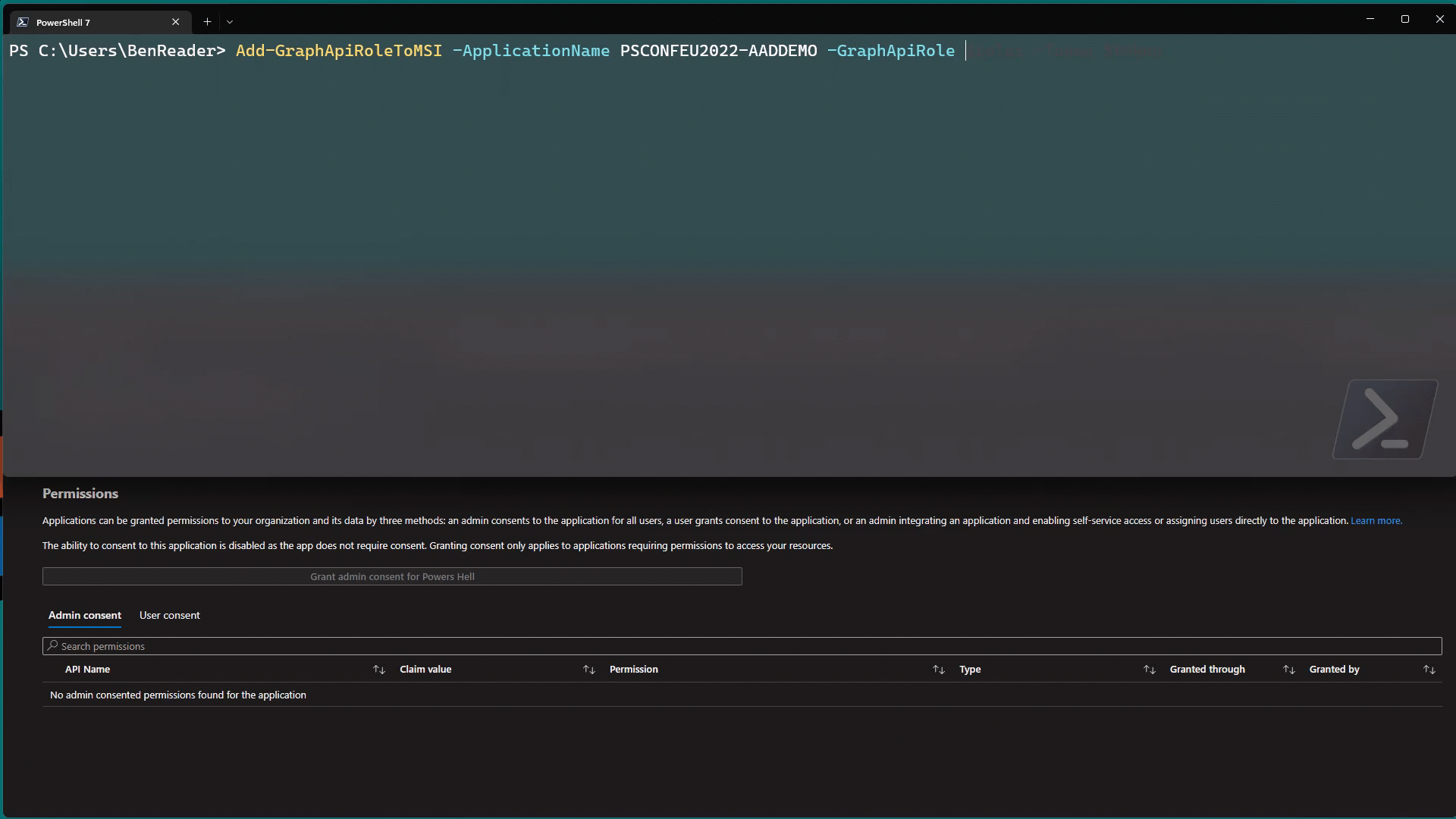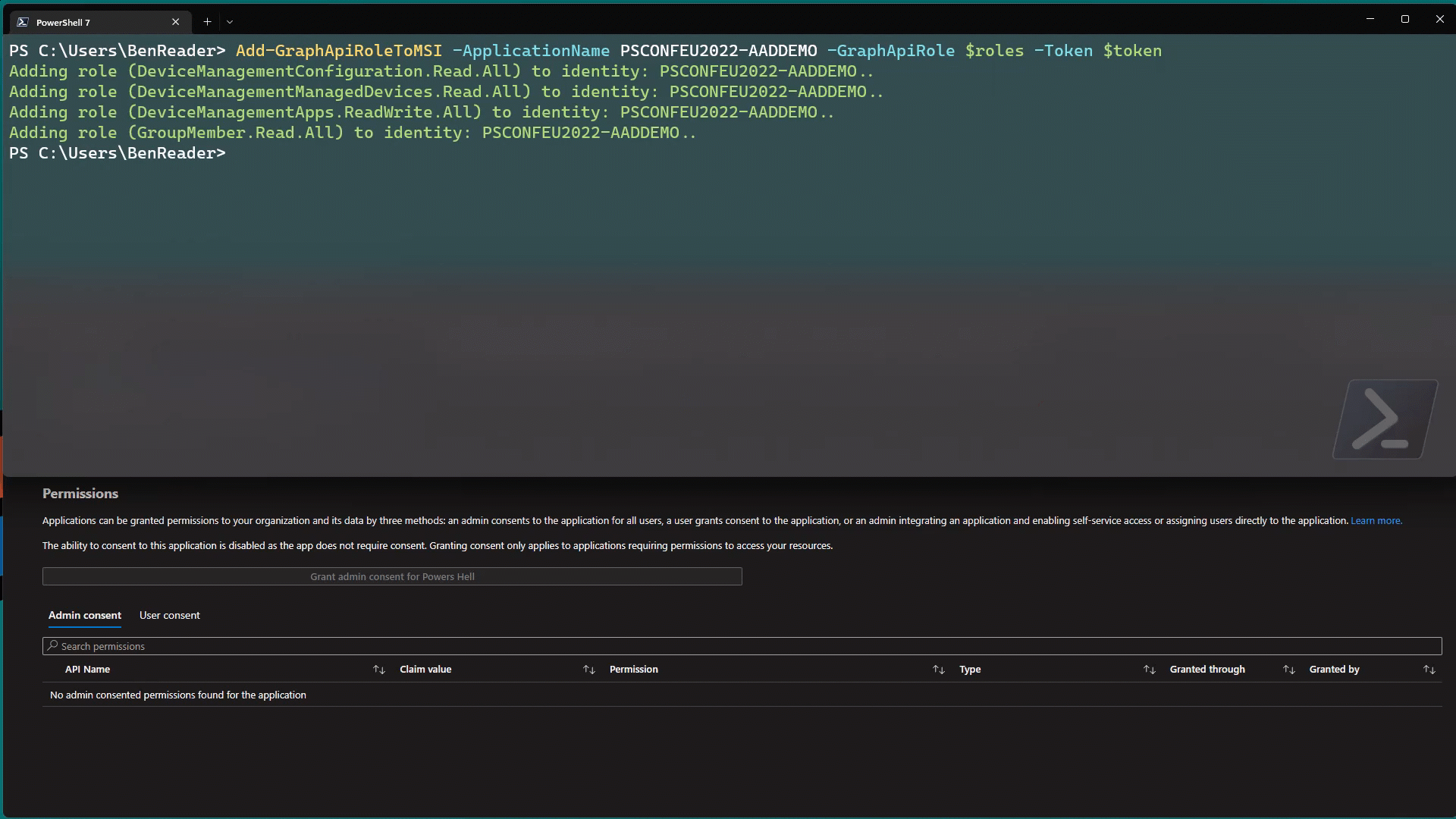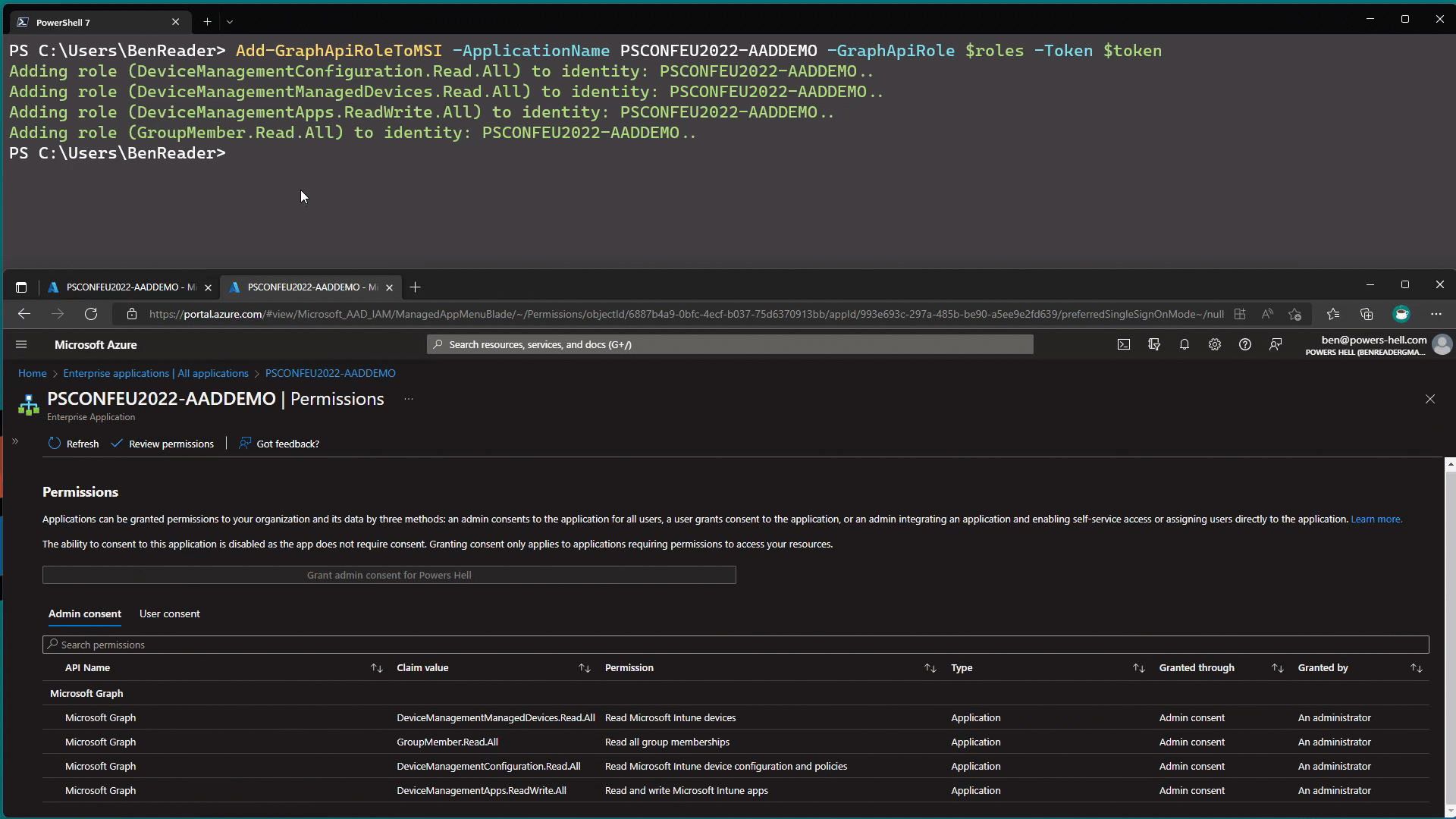
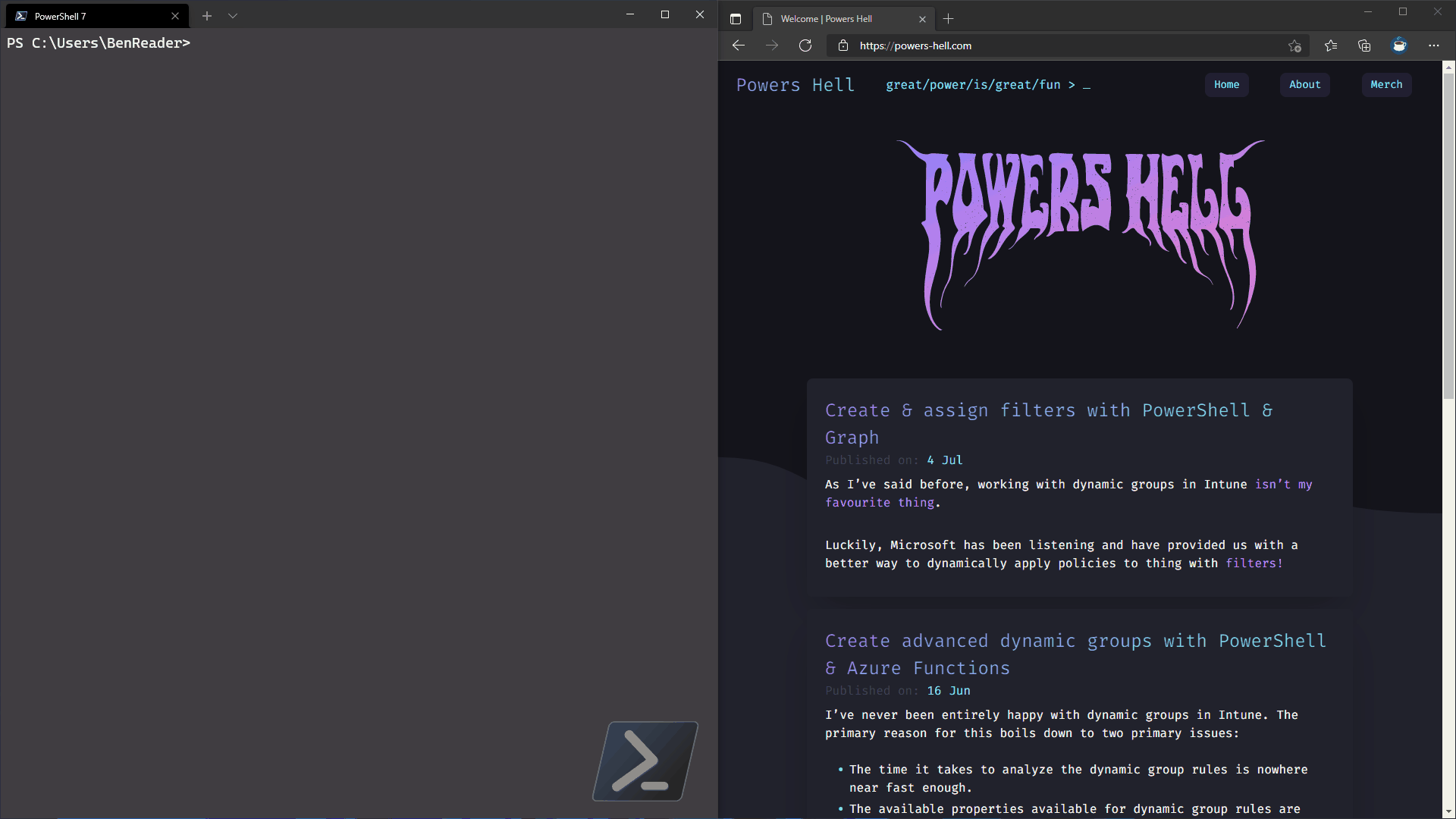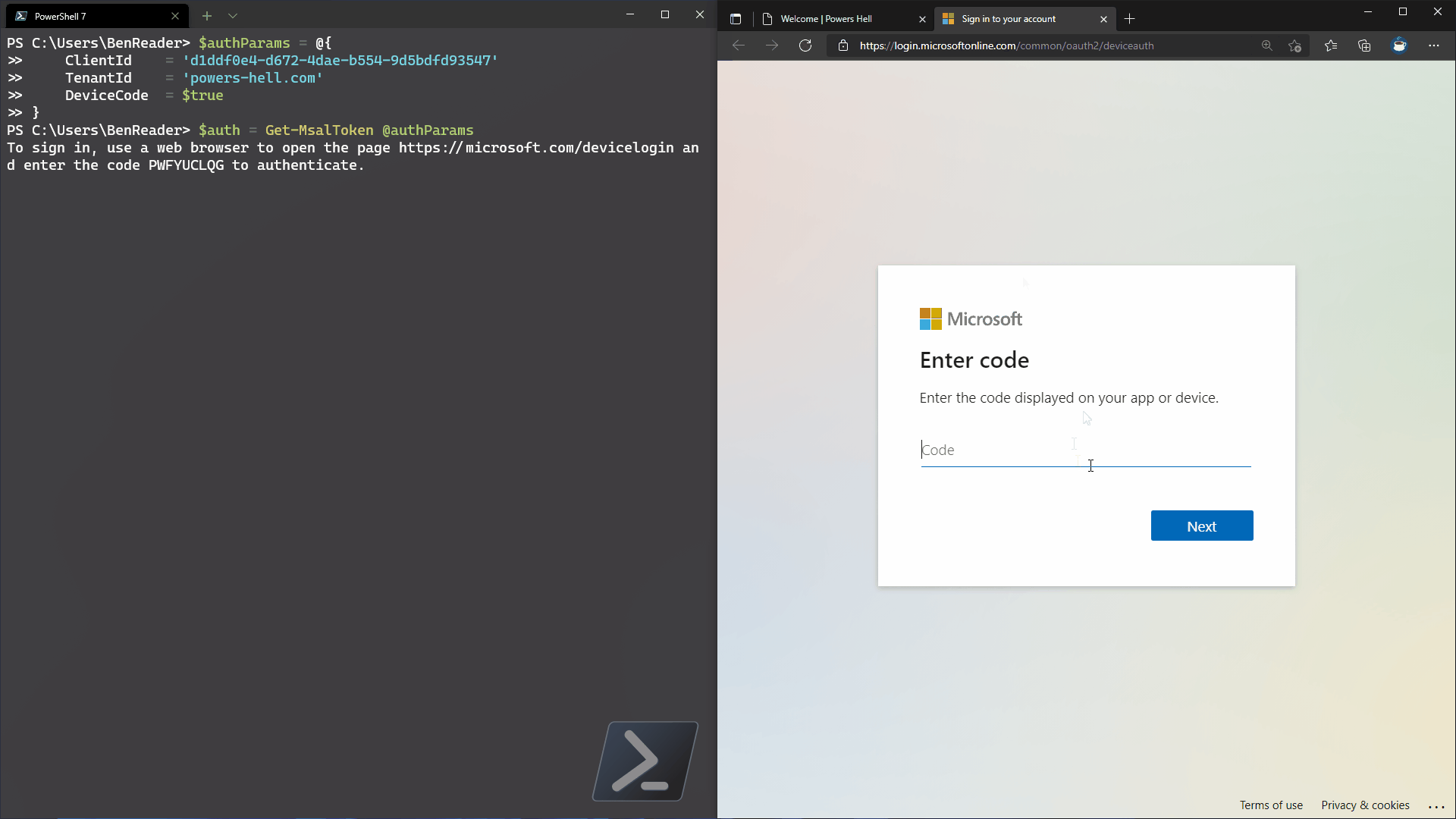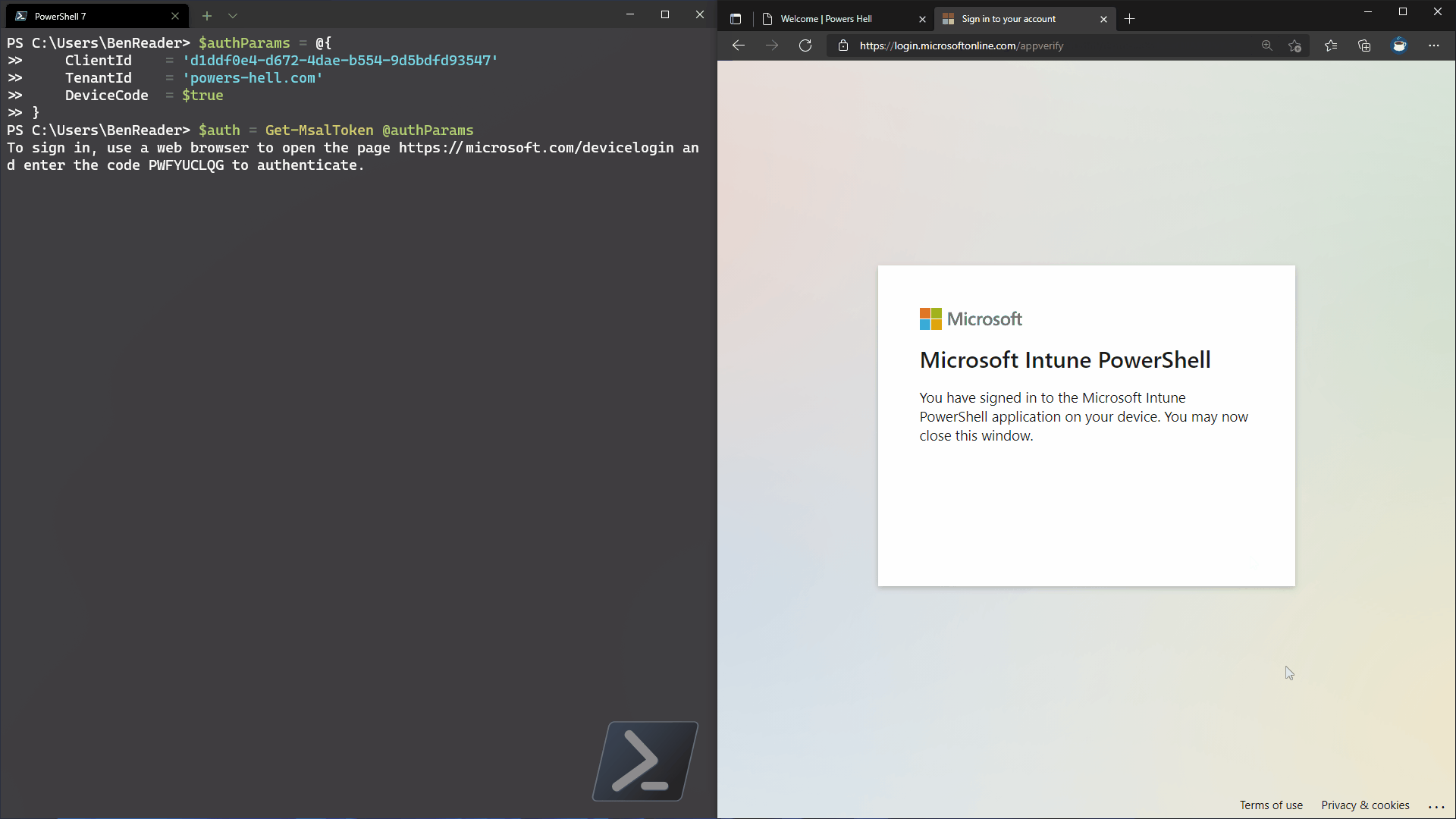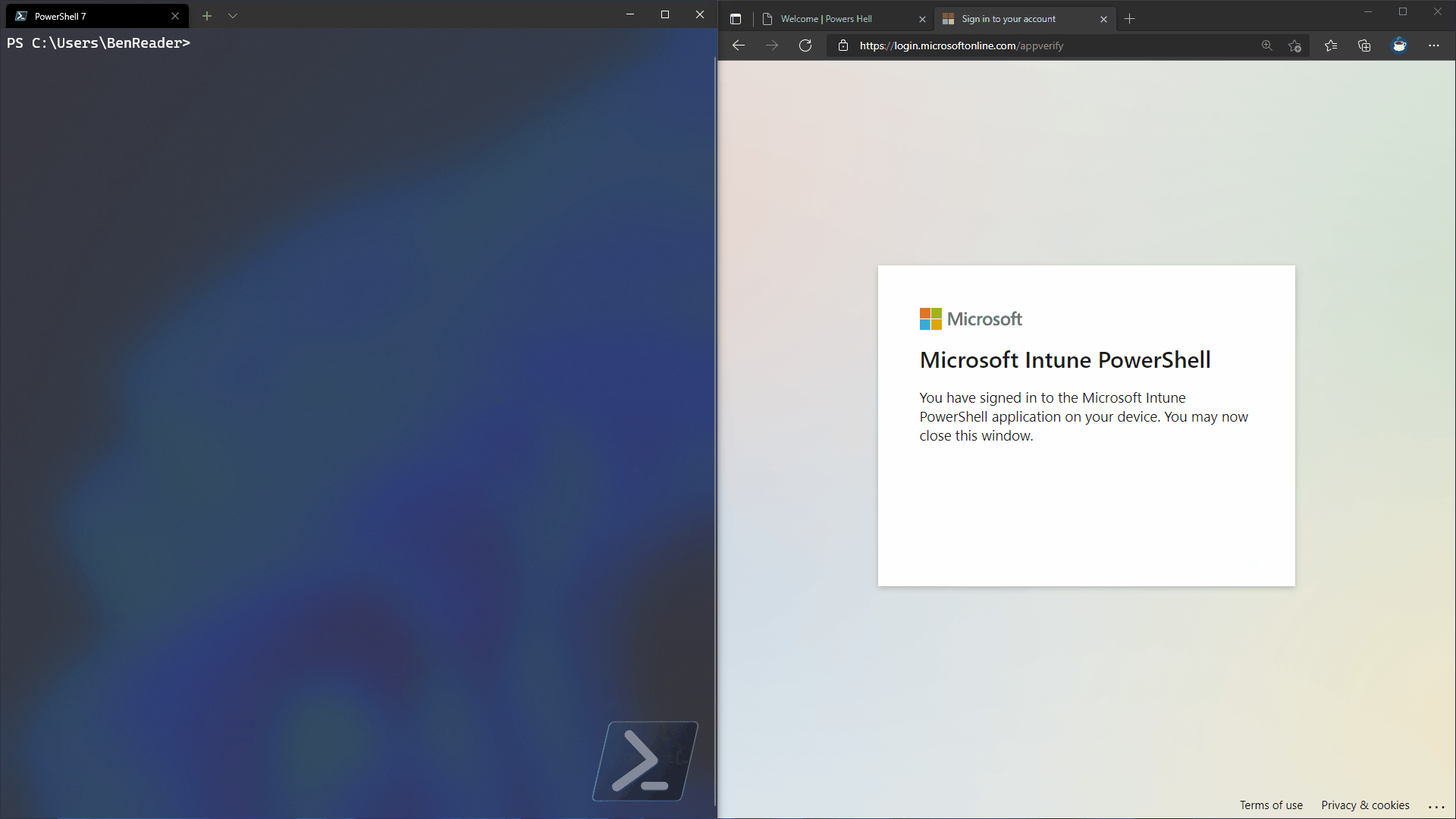
Microsoft has recently announced a new feature that allows us to use managed identities to authenticate across tenants. This is a big deal, and opens up a new secure way of managing multiple tenants in Azure.
One of the biggest security concerns facing developers today is credential leakage and features like this help alleviate the risk of potentially leaving secrets in source control by removing the need for them entirely!
In this post I’ll show you how to set this up to authenticate to a second tenant in an Azure function app, and how to use it to call the Microsoft Graph API!
One of the biggest security concerns facing developers today is credential leakage and features like this help alleviate the risk of potentially leaving secrets in source control by removing the need for them entirely!
In this post I’ll show you how to set this up to authenticate to a second tenant in an Azure function app, and how to use it to call the Microsoft Graph API!
10 minutes to read